Cyber-security and phishing
An increasing number of high-profile organisations have fallen victim to sophisticated cyber attacks as Matt Rhodes from Quiss Technology explains.
Contents |
[edit] Introduction
An increasing number of high-profile organisations have fallen victim to sophisticated cyber-attacks, such as WannaCry back in May 2017 and the more recent ‘Petya’ malware which formed the second major global ransomware attack in just two months.
It is believed that both attacks exploited vulnerabilities within operating systems, having seeded themselves through hijacked software and via phishing emails.
Despite the clear risks, it is reported that around one in ten individuals will still fall victim to a phishing attack, causing disruption to further organisations as a result.
[edit] Constructing a facade
Cyber criminals are well practised in the execution of sophisticated phishing attacks. Creating fake email addresses, criminals are able to impersonate familiar contacts in a credible-looking way, so that they are able to dupe their victim and bypass any security measures that are in place.
Oblivious to an attack, the recipient believes they recognise the email address and opens the email, which contains innocent-looking links. They are prompted to click links which direct them to a convincing, yet fake, website where sensitive information can be extracted.
The email may include toxic attachments containing malware or ransomware. If opened, the device becomes infected and grants criminals access to an organisation’s data.
Criminals continue to find new ways to exploit the weakest point in any system — the people that use it.
[edit] Phishing bait
Even when an email seems to have been sent by a known contact, determine:
[edit] The sender
Are you sure you recognise the sender? Is their email address legitimate or just similar to one you’ve seen before?
[edit] Subject
Does the subject line correspond to the body of the email? Does it look unusual? Is it poorly written? Any subject lines that seem out of the ordinary could be an indication of fraudulent or spam email so look out for spelling mistakes or an excessive use of punctuation.
[edit] Content
Be cautious if an email asks you to enter personal information, requests a reply or encourages you to visit a website.
[edit] Links
Links in emails can easily be disguised to look genuine but may take you to a malicious website, so think twice before you click.
[edit] Attachments
If there are any documents attached to the email, were you expecting it? Is the attachment mentioned in the email? Do you recognise the format? Only open attachments when necessary and do so with caution as they can easily transmit viruses.
Trends in attack methods change frequently so it would be foolish to assume you know what to expect. Anyone can be outwitted by a criminal so don’t get complacent; the outcome could be disastrous.
[edit] The odds are against you
Phishing is favoured by criminals as it has a high success rate whilst being low in risk, and:
- 10% of people targeted fall for a phishing attack.
- 23% will open the message.
- 11% click on attachments.
- 250% increase in the total number of phishing sites from October 2015 to March 2016.
- 91% of hacking attacks begin with a phishing or spear-phishing email.
- 55% increase of spear-phishing campaigns targeting employees.
[edit] Phishing for flaws
Replicating real attack methods, specialist service providers can identify weaknesses in company security systems and train its employees on how to protect themselves from falling victim to phishing emails.
Responses and actions taken are recorded to reveal who opened the emails, clicked links or downloaded attachments, etc.
An email is sent to anyone who interacts incorrectly with the ‘phishing’ email, making them aware of their error and reminding them to be more vigilant in the future. Weaknesses are revealed in a report, enabling businesses to concentrate training where it’s needed most.
Initial failure rates of around 33% will fall to approximately 5%. Unfortunately, a 0% rate is unlikely to ever be achieved as we are dealing with humans.
[edit] Conclusion
Introducing more technology is unlikely to help reduce the risks posed by a phishing attack. The only reliable solution for any organisation is to regularly test defences and to work on changing its security culture.
Targeting employees with ‘fake’ phishing attacks is an effective way to reveal weak links and help resolve them, but businesses should act fast — it’s only a matter of time before the real criminals show up.
This article was originally published here in AT Journal edition 124. It was written by Matt Rhodes, Quiss Technology.
Matt’s primary role is to expand the hosted solutions division of Quiss Technology and to liaise with software vendors to help them develop their Software as a Service (SaaS) offering. He is a regular commentator on industry topics, covering subjects as diverse as cyber security, hybrid cloud solutions, new technology and the Code of Connection (CoCo).
--CIAT
[edit] Related articles on Designing Buildings
- Articles by CIAT on Designing Buildings Wiki.
- Cyber hygiene.
- Cyber resilience.
- Cyber security and engineering.
- Cyber threats to building automation and control systems.
- Digital communications and infrastructure dependencies.
- Engineering resilience to human threats.
- Infrastructure and cyber attacks.
- Information and communications technology in construction.
- Mitigating online risk.
- Protecting against online crime.
- Security and the built environment.
- UK organisations encouraged to review cyber security in response to situation in and around Ukraine.
Featured articles and news
Key points for construction at a glance with industry reactions.
Functionality, visibility and sustainability
The simpler approach to specification.
Architects, architecture, buildings, and inspiration in film
The close ties between makers and the movies, with our long list of suggested viewing.
SELECT three-point plan for action issued to MSPs
Call for Scottish regulation, green skills and recognition of electrotechnical industry as part of a manifesto for Scottish Parliamentary elections.
UCEM becomes the University of the Built Environment
Major milestone in its 106-year history, follows recent merger with London School of Architecture (LSE).
Professional practical experience for Architects in training
The long process to transform the nature of education and professional practical experience in the Architecture profession following recent reports.
A people-first approach to retrofit
Moving away from the destructive paradigm of fabric-first.
International Electrician Day, 10 June 2025
Celebrating the role of electrical engineers from André-Marie Amperè, today and for the future.
New guide for clients launched at Houses of Parliament
'There has never been a more important time for clients to step up and ...ask the right questions'
The impact of recycled slate tiles
Innovation across the decades.
EPC changes for existing buildings
Changes and their context as the new RdSAP methodology comes into use from 15 June.
Skills England publishes Sector skills needs assessments
Priority areas relating to the built environment highlighted and described in brief.
BSRIA HVAC Market Watch - May 2025 Edition
Heat Pump Market Outlook: Policy, Performance & Refrigerant Trends for 2025–2028.
Committing to EDI in construction with CIOB
Built Environment professional bodies deepen commitment to EDI with two new signatories: CIAT and CICES.
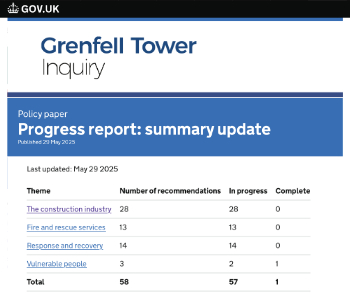
Government Grenfell progress report at a glance
Line by line recomendation overview, with links to more details.
An engaging and lively review of his professional life.
Sustainable heating for listed buildings
A problem that needs to be approached intelligently.
50th Golden anniversary ECA Edmundson apprentice award
Deadline for entries has been extended to Friday 27 June, so don't miss out!
CIAT at the London Festival of Architecture
Designing for Everyone: Breaking Barriers in Inclusive Architecture.
Mixed reactions to apprenticeship and skills reform 2025
A 'welcome shift' for some and a 'backwards step' for others.